Customers are warned about security vulnerabilities in the WP Fastest Cache WordPress plugin, allowing attackers to access website databases through SQL injection. Over 600,000 websites are affected, and users are advised to update to version 1.2.3 or higher to fix the issue. The vulnerability is caused by improper variable checks on user login information. Preventative measures include updating all plugins, using a reliable security plugin, backing up databases regularly, and seeking assistance from web hosting providers if suspicious activity is detected. The article from Nhan Hoa provides guidance on addressing this serious security issue.
Dear customers, if you are using plugins from Nhan Hoa, be aware of security vulnerabilities that could potentially compromise your website. One such plugin, WordPress WP Fastest Cache, has a critical SQL injection vulnerability that could allow attackers to access your database without authentication.
### 1. Overview of WP Fastest Cache
WP Fastest Cache is a popular caching plugin designed to improve website performance by speeding up page loading times and enhancing visitor experience. With over a million websites using this plugin, it plays a crucial role in optimizing websites for search engine rankings.
The current vulnerability, CVE-2023-6063, affects all versions of WP Fastest Cache before 1.2.2, with a severity score of 8.6 out of 10. This vulnerability poses a significant risk to over 600,000 websites still running outdated plugin versions.
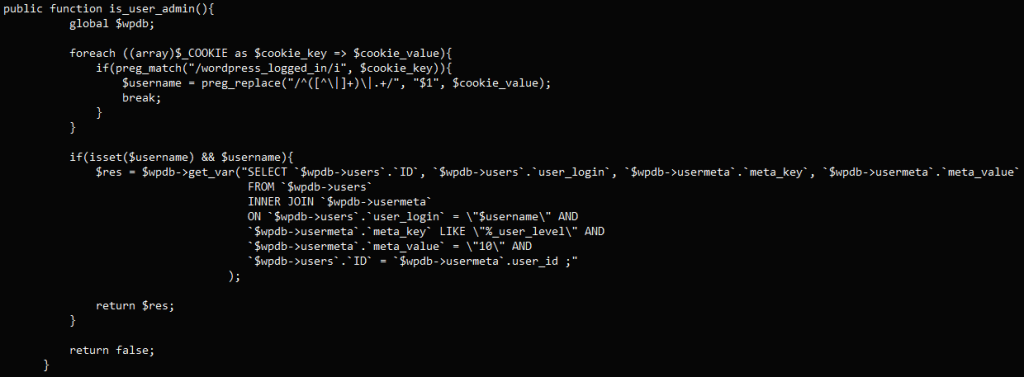
SQL injection vulnerabilities like this exploit software’s susceptibility to input manipulation, allowing attackers to execute unauthorized SQL commands. In this case, the vulnerability targets the ‘is_user_admin’ function of the ‘WpFastestCacheCreateCache’ class, extracting user information from cookies.
### 2. Vulnerability Description
The vulnerability arises from inadequate checks on the variable value ‘$cookie_value’ within the WP Fastest Cache plugin. Attackers can exploit this by injecting malicious SQL code into cookies, enabling them to execute unauthorized actions on the website’s database. This critical vulnerability can be leveraged by any attacker, regardless of their access privileges.
### 3. How to Fix:
To address this vulnerability, users must update their WP Fastest Cache plugin to version 1.2.3 or higher. Additionally, consider implementing the following measures to safeguard your website against CVE-2023-6063:
– Update all WordPress plugins to the latest versions.
– Utilize a reputable WordPress security plugin.
– Regularly backup your website’s database.
If you suspect a security breach on your site, promptly contact your web hosting provider for assistance. For more detailed guidance, refer to the article from Nhan Hoa linked above. Stay proactive in securing your website to ensure its protection. Good luck!